Published Sep 18, 2019
Evaluating the Security of iPaaS Solutions Effectively and Efficiently

Securely integrating your SaaS applications
Is evaluating the security of iPaaS solutions unnecessarily prolonging your progress towards application integration and optimizing your processes?
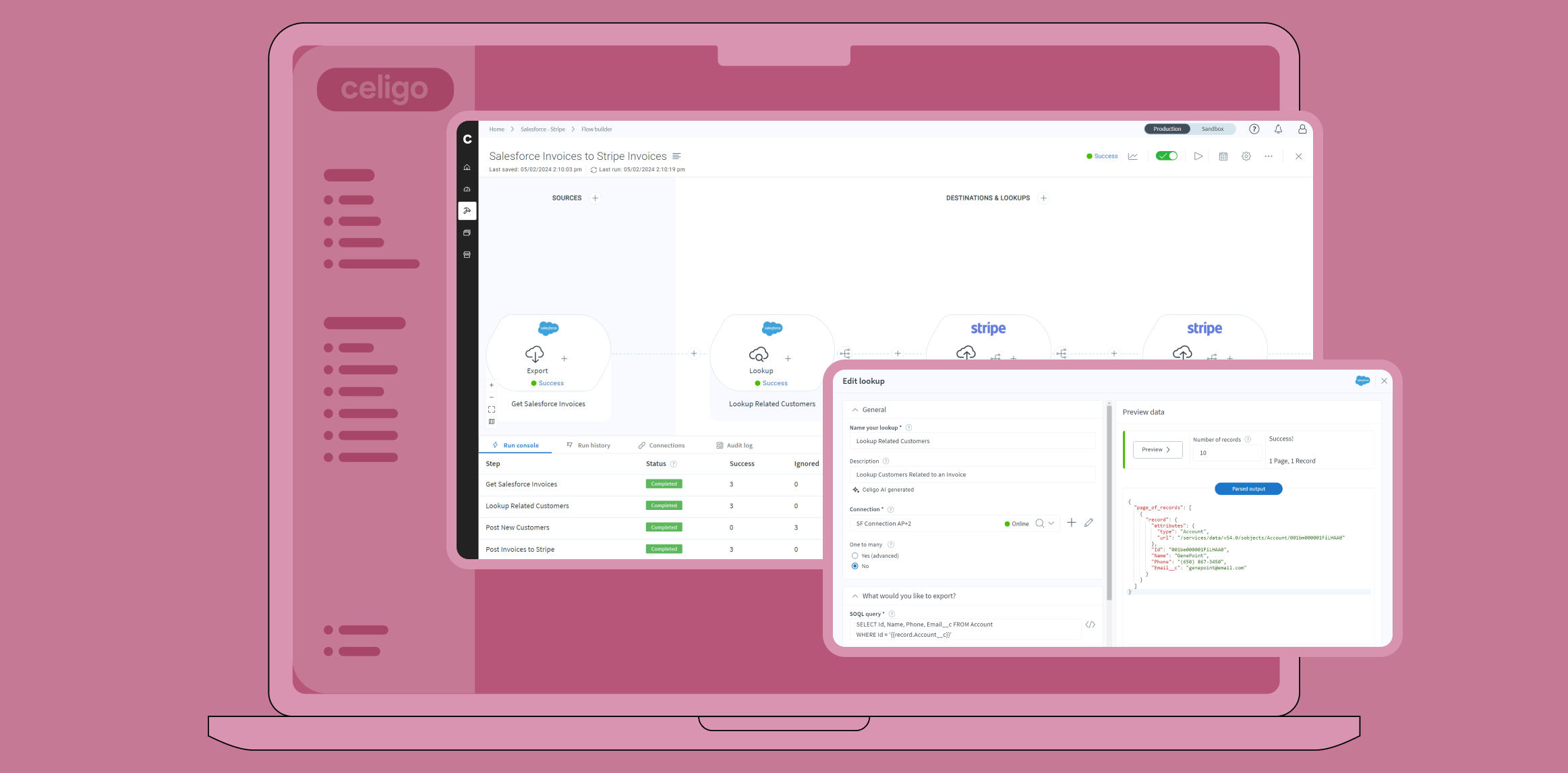
Not familiar with iPaaS? Read: “What is iPaaS?“.
Nowadays, most modern medium to large companies, along with a growing number of smaller ones, are strong users of multiple SaaS solutions. As a result, integrating those applications to optimize business processes is of critical importance to ensuring the efficiency of a company as a whole.
Part of the process for selecting any new service provider(s) is performing due diligence to make sure that applications run securely and work together. If they don’t natively integrate, determining how to integrate the solutions can be fraught with challenges.
If no convenient or turnkey solutions exist, designing and developing custom integrations comes at a high price. Not all businesses have the resources to develop these in-house, and so must bring in contractors which only bumps up the cost. If the expense of development wasn’t high enough, maintaining these custom integrations brings the price tag over the edge for most businesses looking to expand.
There’s a new player in town
Integration Platform as a Service (iPaaS), has come into its own, and can easily and quickly integrate your SaaS solutions! No need for heavy IT involvement in many cases, and this lowers the time to integrate, and therefore the costs.
However, as with your SaaS applications, you must select an iPaaS provider carefully by performing meticulous due diligence. The iPaaS provider handles your sensitive data while it is in transit and processing between applications, so data security is extremely important when selecting an iPaaS.
As with SaaS solutions, ask yourself the following questions: What data is being moved or processed? Is it sensitive or PII under regulatory requirements? (GDPR, Privacy Shield, HIPAA, PCI and FERPA to name a few!) Most importantly, is the data being stored securely or persistently?
Many of the regulatory requirements mandate that data be handled in specific ways for security. Of course, encryption is an extremely important aspect, even if not a strict requirement (only a few of the standards actually require encryption at rest for instance.)
How we usually evaluate security
When performing due diligence, you’re going to be asking questions — sometimes a great many questions! What do your Questionnaires look like? Are they very large? Do they have evidence required? Are they based on the same questionnaires used for the major SaaS providers?
Large questionnaires can take a great deal of time for a proposed vendor to respond to. You are looking at potentially weeks of work, and thus significantly impacting how long it takes to complete the selection process, much less even start the integrations!
Business needs to move at speed! Full audits are a slow bureaucratic process…
And wait: Does your proposed iPaaS integration provider store the data persistently? Or is it pass-through only?
The risk may not be the same as a SaaS solution where they DO store the data persistently. The risk with iPaaS security should be very limited compared to a SaaS solution that is persistently storing most of the data about your business, not to mention the data on your customers or maybe even your customer’s data! The due diligence should be commensurate with that risk.
How Can This be Done More Efficiently?
Due diligence can take on many forms.
Like you, I am also involved in evaluating sub processor vendors (some SaaS, some are other technical service providers) and I always start by requesting their SOC reports.
What is a SOC Report You Ask?
A SOC report is the report of an independent auditor who has audited the service provider in question and reported on the results according to the SOC Trust Services Criteria. The SOC Trust Services Criteria is an auditing standard that the American Institute of CPAs (AICPA) developed for evaluating service providers.
A SOC 1 is for Financial Services (replacing the SAS-70), and SOC 2 is for any other class of service—most SaaS and iPaaS solutions fall under this one—and SOC 3, which is a redacted report that can be published publicly. These reports may be provided as Type 1 (test of design) and Type 2 (test of effectiveness). The SOC 1 and 2 reports can only be shared—under NDA—with auditors, customers, and prospective customers. You really don’t want the general public, including potential hackers, to have access to the full reports.
These audits investigate providers at a much deeper level than an ordinary due diligence questionnaire, with far more evidence required to complete the audit. This includes a full description of the service, how it is managed, how it is secured, so you are getting most, if not more, of your due diligence done for you in a report you can easily see if the service has issues you should be concerned with.
This will usually close the book on most any questionnaire, and do so quickly!
Due Diligence!
In a nutshell, properly reviewing the SOC 2 report IS due diligence!
So, to get started with actual integrations sooner:
- Start with a request for a SOC 1 or 2.
- Review the report in detail
- If a questionnaire is still needed, here are some tips to get answers back quickly:
- Tailor it for the iPaaS Integration, NOT the generic one you would use for a SaaS.
- Answer the questions with what you learned from the SOC 2 report—contact the prospective service provider to verify any points.
- Group the questionnaire so sections can be skipped based on responses.
- For example, “do you store data persistently? (If no, skip Questions 18-25)
- Be sure to include a place for comments even for Y/N questions.
- Not every response is a simple Y/N so more explanation is needed.
- A comments area is a way to avoid confusion and the resulting back and forth emails
- Other things to consider for Sensitive Data/PII:
- Do you have GDPR data considerations—if in the EU, or doing business with the EU, you need a service provider that is “GDPR Ready” and to sign a Data Protection Agreement/Amendment (DPA), or, the service provider can be under the US Privacy Shield
- Is there Payment Card (PCI) data?—is the Service provider PCI-DSS Compliant?—Certification is required
- Is there HIPAA (Health) ePHI data?—A Business Associate Agreement (BAA) is needed
- Other PII concerns? Know your requirements!
In Conclusion
Remember, business needs to move quickly! Taking too much time implementing iPaaS prolongs the issues you are trying to solve with integrations. Fortunately, you can use the tips outlined in this post to help speed up due diligence while also ensuring that your data is kept secure.
Make use of SOC 1 or 2 reports to more efficiently evaluate iPaaS security of your prospective vendor – happy integrating!